SOC services: Detect and respond to cyber threats 24/7 without overwhelming your IT team
We respond immediately to any threat with our Blue Team and Intelligence Unit, monitoring, detecting and analyzing incidents in real time. We centralize security and administration tools with our SOC (Security Operations Center) service.
Protect your companyBenefits of a SOC service for businesses
Cybersecurity cannot depend on sporadic reviews or automatic alerts that no one checks. If you identify with any of these challenges, it's time to evolve your defense:
Book demoWhy do you need a SOC service?
According to TrendMicro and SANS (2023), well-implemented SOCs help reduce incident response time and align the security operation with the business strategy. Discover all that your company can receive with a SOC managed by Delta Protect:
Book demoComparison of Internal SOC vs. Outsourced SOC Service


All about SOC as a Service

Security Operations Center is a managed security operations service that uses advanced technologies such as Artificial Intelligence (AI) and Machine Learning (ML) to detect, contain and mitigate cyber threats in real time, ensuring the continuity and protection of your business.

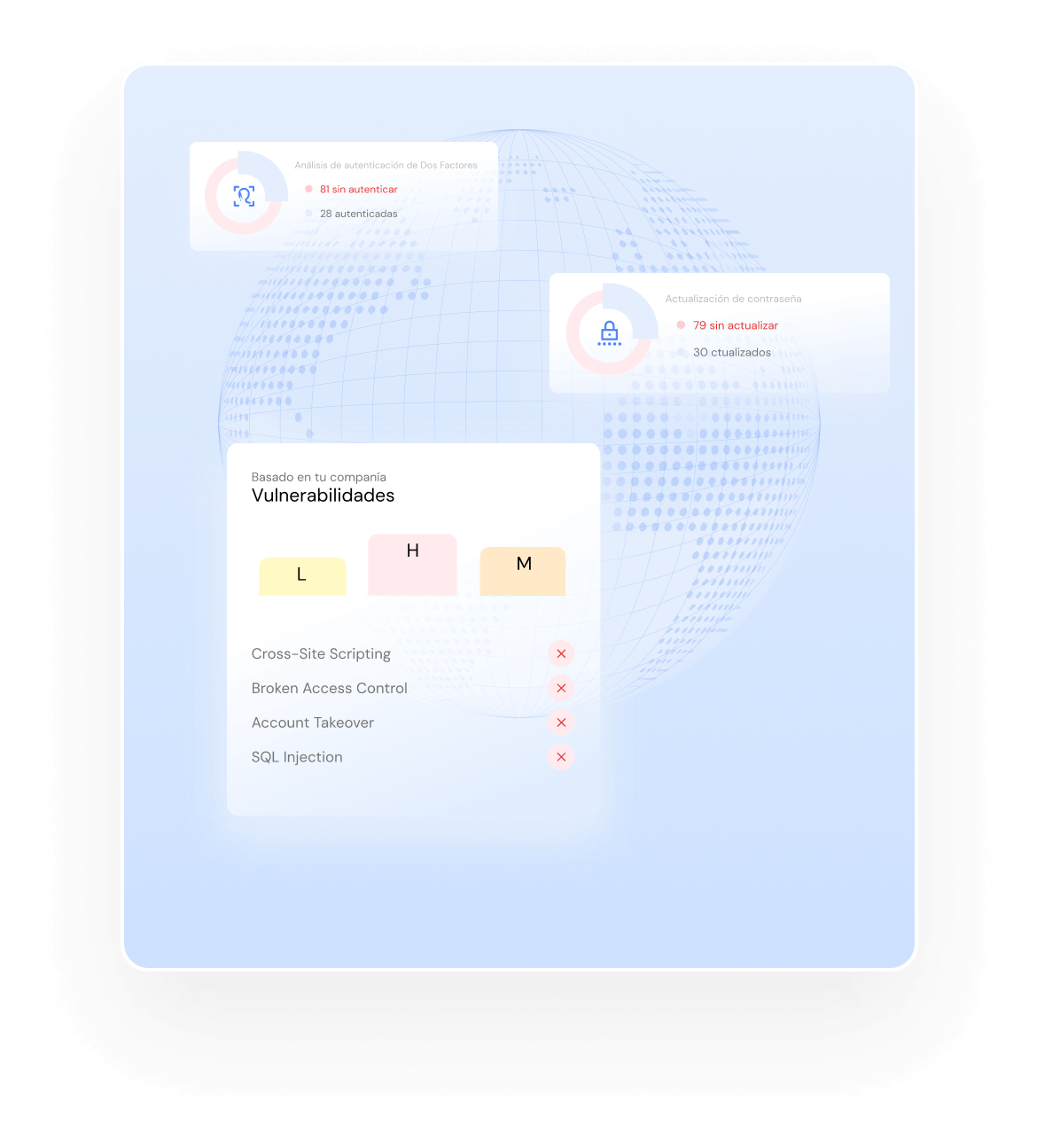
Security Operations Center provides continuous monitoring, rapid threat detection and effective incident response, with the help of cybersecurity experts and advanced tools. Your company will be better protected against attacks such as malware, ransomware and zero-day threats.

Our Security Operations Center can handle a variety of cyber threats, including malware, ransomware, zero-day attacks (Zero Day), advanced persistent threats (APT), brute force attacks, data leakage, insider threats, and attacks on cloud services and denial of service.

Yes, the Security Operations Center is scalable and can adapt to the needs of companies of all sizes, from small and medium-sized enterprises to large corporations, providing a flexible and adjustable solution according to the growth and security demands of your business.

The Security Operations Center eliminates the need to invest in expensive infrastructure and specialized personnel. It provides access to cybersecurity experts, real-time detection and response, and a scalable solution that reduces capital and operating costs. It also ensures ongoing regulatory compliance.

To choose the best SOC service for your company, you need to consider the following factors: 24/7 monitoring, technology used, SLAs, team experience, regulatory compliance, and modularization.

You need a Security Operations Center to ensure the security posture of your business in an increasingly dangerous digital environment. With the increasing sophistication of cyber threats, a Managed Security Operations Center service provides you with immediate access to cybersecurity experts and advanced technologies such as Artificial Intelligence and Machine Learning. This ensures early detection and rapid response to any threat, protecting the operational continuity and integrity of your data.
In addition, by opting for a Security Operations Center, you eliminate the burden of managing costly infrastructures and specialized teams in-house, allowing you to focus on your core business while maintaining a consistent compliance and proactive security strategy.

When choosing a Security Operations Center service provider, it is crucial to evaluate several aspects to ensure that the solution fits your business needs and objectives. Below are some key considerations:
Detection and response capabilities
Ensure that the service provider can detect and respond to a wide range of threats. Verify the use of advanced technologies such as Artificial Intelligence (AI) and Machine Learning (ML) to improve detection accuracy and speed.
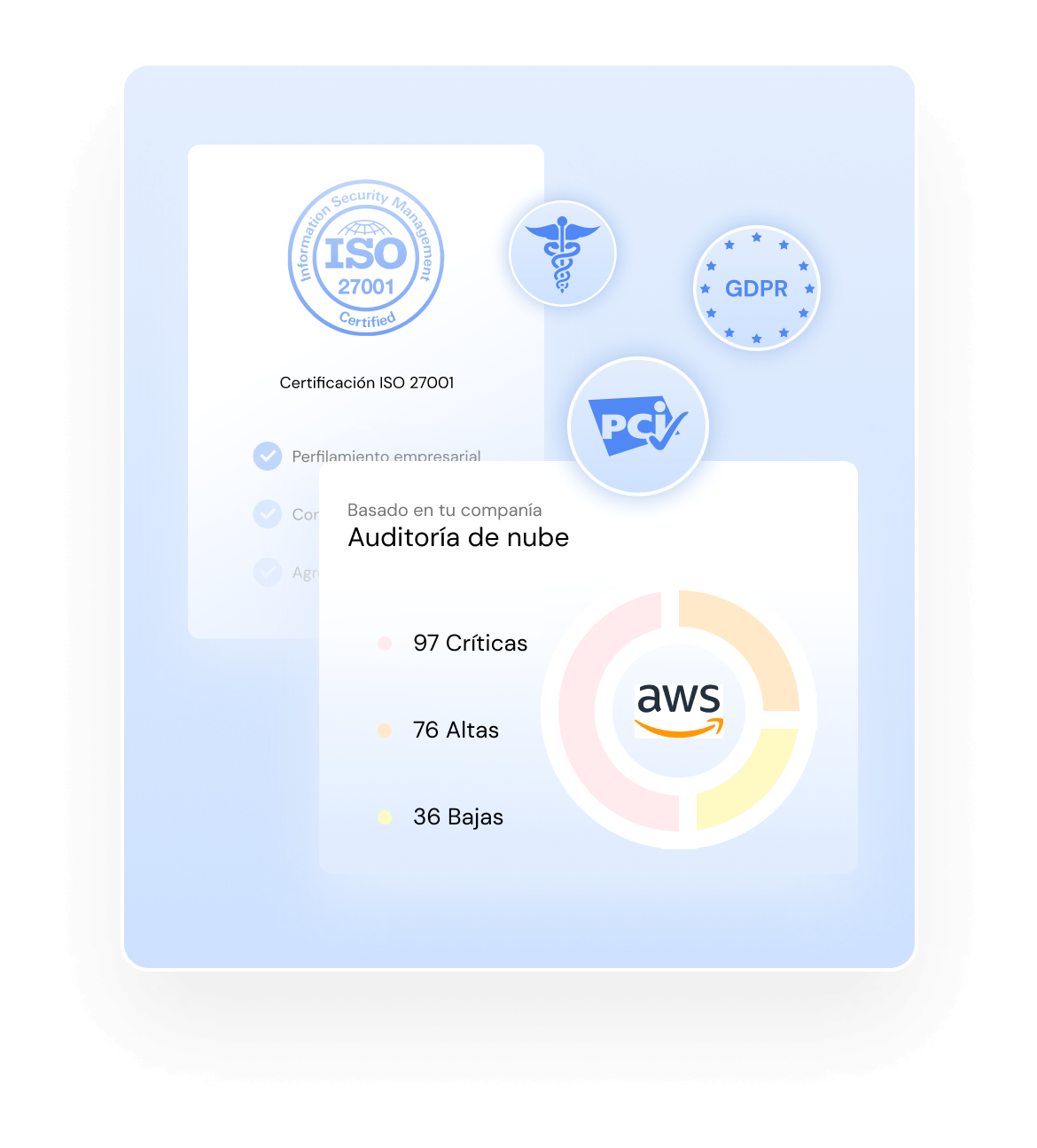
2. Regulatory compliance
Verify that the Security Operations Center complies with security regulations and standards relevant to your industry, such as PCI-DSS, NIST, HIPAA and ISO 27001.
3. Focus on Zero-Trust
The vendor should adopt a Zero-Trust approach, verifying and monitoring every access and activity to minimize security risks. This is critical to avoid alert fatigue and improve security posture.
4. Scalability and flexibility
The solution must be scalable to adapt to the changing needs of your business.
5. Experience in security services
Evaluate the vendor's experience and expertise in cybersecurity. A good provider should have a security team with in-depth and up-to-date knowledge of cyber threats and security best practices.

The operation of a SOC is based on total visibility and immediate response. Instead of waiting for an attack to occur, the SOC team proactively monitors all network activity using threat intelligence tools. When unusual activity is detected, the SOC acts according to this cycle:
Monitoring: Uninterrupted surveillance of all digital assets.
Correlation: Cross-referencing data to identify complex attacks.
Containment: Immediate isolation of compromised devices.
Recovery: Assistance in returning to normal operations after an incident.
Contact us and start protecting your company
Take the next step to become a more cybersecure company.